2022 Cybersecurity Awareness Month Hub
Resources to help your company monitor and manage the risk of cybersecurity threats

It's Cybersecurity Awareness Month!
Dataprise is sharing a series of relevant content to help educate and protect your organization against the latest cybersecurity attacks.
Join us throughout the month for tips and strategies to help increase your cybersecurity awareness, while we follow the story of Johnny M., aka V1P3R, a hacker ready to exploit Soar Design's corporate data.
Are you ready to think like a hacker?
Our VP of Cybersecurity Services, Stephen Jones, speaking on the importance cybersecurity awareness month can bring to organizations that might not be as prepared as they need to be right now.
Meet Johnny M., aka V1P3R

Meet Johnny M., aka V1P3R. He's a hacker with a LOT of time on his hands to infiltrate your business.
He's what you'd consider a black hat hacker and can drive your business to ruin in one energy drink's time.
Aside from hacking, Johnny spends his time learning all he can about the latest technologies and understanding how things work. Generally, that leads to him learning how to hack into it, but nevertheless, he's an avid learner.
Over the course of the month, we'll take you on a journey in the life of Johnny M. and how he approaches hacking into corporate data.
Week 1 - Protecting the User
It’s the start of a new quarter, and Soar Designs is ready to start strong. As an architectural design firm, they have a large pipeline of customer projects they are looking to wrap up before the end of the year and they are on track to have their best financial year yet.
Johnny M. sees this as an opportunity.
Howard, an ever-busy Project Manager at Soar Designs, is juggling managing 5 different large builds while personally preparing for a move to a new home and getting used to month 6 of being a new dad. Needless to say, Howard’s a little tired.
Johnny M. knows that the Project Managers at Soar Designs most likely have access to key systems, including accounting software for budgeting purposes and architectural designs. He shoots his shot with an attempt at phishing Howard with a convincing email citing suspicious account activity:
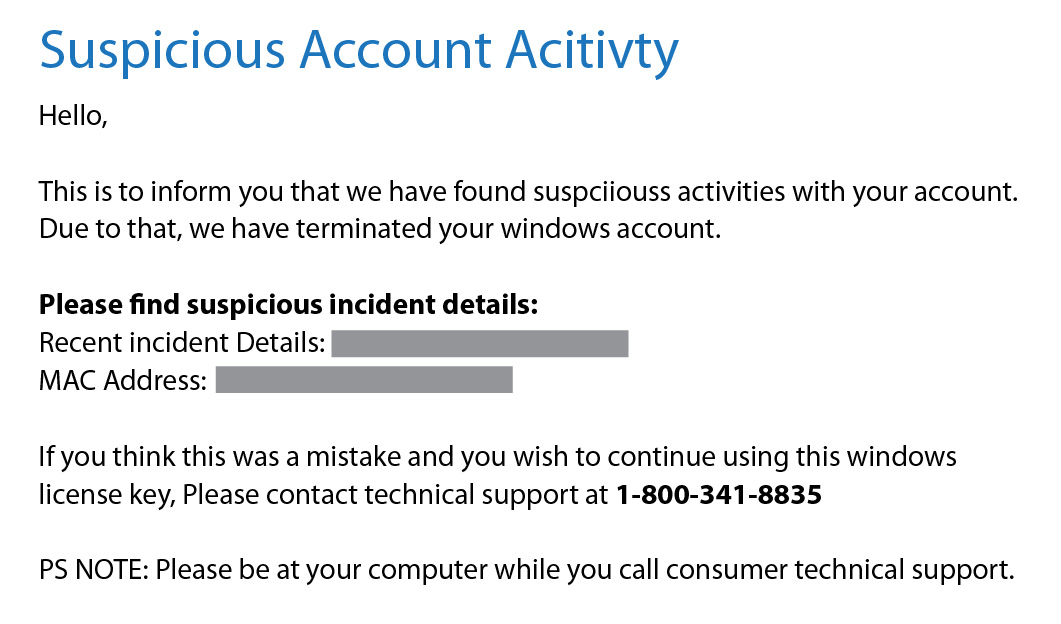
Howard, in the 3 minutes he has between customer calls, eating a 12pm breakfast, and answering chats from his design engineers, takes a quick look at the email and signs in to help address the issue.
And with that, Johnny is in.... or so he thinks.
Resources to Protect Your Users
Don't let your employees be like Howard- view our resources below to help educate your end-users on cybersecurity attacks.

Video Clip - What are some common pitfalls that organizations trust users too much for?
Watch our expert, Stephen Jones, discuss 3 ways that organizations trust users too much in.

Blog Article - 10 Cybersecurity Tips Every Employee Should Know
Click here to read 10 cybersecurity tips that employees should practice and know.

Video Clip - Where are cybersecurity compliance and regulations headed?
Learn from our expert Stephen Jones on where cybersecurity compliance and regulations are going in 2023 and beyond.

Cybersecurity Best Practices: Protecting Against Malicious Emails
A list of what employees should look out for when handling emails to avoid being a victim of an attack.

Strengthening the Human Firewall
What is your organization doing to combat security breaches caused by human error? Read our 5 questions your stakeholders should be asking.
Week 2 - Protecting the Organization
So, last week, we left off with Johnny M. phishing Howard. Howard is in the middle of a day filled with back-to-back customer calls. Not fully reading the email in his inbox, he clicks through and signs in to help with the issue that Johnny “presented” to him. Johnny M. is ready to believe that he has tricked Howard, and is able to access Soar Designs' sensitive data. BUT… Enter Karla.
Karla is one of Soar Designs' IT Managers. Karla is in charge of managing their infrastructure and network.
Karla and her team are implementing Zero Trust Network Architecture Model (ZTNA) on their IT environment, and they are alerted to a threat occurring!
ZTNA is a security framework requiring all users, whether in or outside the organization’s network, to be authenticated, authorized, and continuously validated for security configuration and posture before being granted or keeping access to applications and data. Check out our full blog article on ZTNA strategies.
Unfortunately, Karla and her team do not realize that Johnny M. has discovered a server that was WAY past an upgrade date. Oftentimes, legacy systems tend to be used because of their attachment to one critical part of the business, and cannot be replaced.
Johnny is aware that he can successfully exploit this vulnerability and now, begins to access all of Soar Designs' corporate data.

Resources to Protect Your Organization
Karla thought that she had her bases covered - but she didn't. View our resources below to help protect your organization cybersecurity attacks.

Video Clip - What are common gaps in an organizations Incident Response plan?
Watch our expert, Stephen Jones, identify common gaps in an organizations Incident Response plan.

Blog Article - Top Attacks Your Organization Should Prepare for in 2023
Click to read the top 6 attacks your organization should prepare for in 2023.

Video Clip - What is an example of a security awareness training topic organizations should have in place for their users?
Watch our expert Stephen Jones speak on security trainings - particularly around phishing.

CIOs Ransomware Checklist: Before, During & After an Attack
Download our CIO's Guide to Ransomware Checklist and complete our checklist to best prepare for before, during, and after an attack.

Getting Started with Zero Trust: Implementation Considerations
ZTNA is s a cybersecurity model that helps companies avoid risky interactions between users, machines, and data — regardless of where the threat comes from.
Week 3 - Responding To An Attack
Picking up where we left off, Karla, Soar Designs’ IT Manager detected that Johnny M. had breached Soar Designs’ sensitive data. Karla was alerted to the threat and put a stop to Johnny M going any further. Unfortunately, due to an outdated server, Johnny M. was able to maneuver around to access all of Soar Designs’ data.
This outdated server, which is tied to a critical part of the business, does get monitored even though it is not protected like the rest of the network. Luckily, Karla is alerted (albeit late) to the fact that an attack is actively occurring.
Karla and her team are enacting their incident response plan to mitigate the impact and attempt to stop the attack. Incident Response Plans create a framework for how cyber teams detect, respond, and recover from a security incident.
However, it is too late – Johnny M. had access for long enough that he has already gotten all the data he needed from the servers. With Soar Designs’ corporate data in hand, Johnny’s next move is to set a ransom for Soar Design to get their information back.
Resources to Respond to An Attack
Organizational preparedness is a massive undertaking - view our resources below to prepare your organization efficiently and effectively.

Video Clip - What Does Having a BCDR Strategy In Place Do In Terms of Responding To an Attack?
Dataprise VP Stephen Jones explains why your organization should be implementing a BCDR Strategy to optimize responding to a cyber attack.

Blog Article - What To Do First in A Cyber Incident
The cost of a data breach continues to grow year after year. Read our latest blog on what to do first in a cyber incident, so you can mitigate damage your organization may take.

Video Clip - What Is The First Thing You Should Do When Your Organization Is Hit With Ransomware?
Studies show that cyber incidents rise during the holiday season. Check out our latest from our subject expert, Stephen Jones.

CIOs Guide to Disaster Recovery Planning + BCDR Tabletop Exercise
Download our CIO's Disaster Recovery Planning Guide with a bonus tabletop exercise for your staff to complete to measure your current environment.

Blog Article - 2022 Cybersecurity Spending Trends
Take a look back at our blog from earlier this year highlighting spending trends in Cybersecurity in 2022 and beyond.
Week 4 - Recovering from an Attack
Johnny M. was able to successfully access sensitive company data by infiltrating an outdated server, which is still in place because of a certain legacy system that Soar Design relies on. Johnny M. then took this data and encrypted it, with his next move being to set a ransom for Soar Design to get access to their information back.
With the data in hand, Johnny M. maliciously reaches out to Karla and her team at Soar Design, declaring that he will leak their corporate data if they do not comply with his ransom request. But luckily...
Soar Design has an incident response plan in place and has notified its cyber team. The cyber team works hard to begin restoring this sensitive data through backups that had ransomware protection in place. With the backups kicking in and the data being restored, Johnny M. has no more leverage and is forced to retreat, with no ransom payment.
With the backups fully restored, Karla provides an update to Stacey, head of the executive team, on what occurred. Stacey, with way more than just IT on her mind, begins to realize that it is a priority to tighten up their systems, as, without the Incident Response Plan in place, Soar Design would have suffered severe financial and reputational loss from the downtime. Karla and Stacey discuss further and decide it is time to tighten up their systems and perform a security assessment of their systems with the help of a cybersecurity services provider to bring their environment in line with current best practices and procedures.
Resources to Recover from an Attack
Recovering from an Attack is a big undertaking. It is important that your organization is prepared when the time comes, as you want to be able to efficiently and effectively tackle the problem.

Video Clip - Top 3 Things Organizations Should Know About Cybersecurity Insurance
Dataprise VP Stephen Jones explains why your organization should be implementing a BCDR Strategy to optimize responding to a cyber attack.

Blog Article - 3 Proactive Measures to Expedite Cybersecurity Incident Recovery
Outages of any kind that affect business continuity are a major threat to organizations, as they can result in financial loss, confidential data loss, and more. Ensuring a speedy recovery following a cyber incident is critical. Read our latest blog article below.

Video Clip - What Is The Top Cybersecurity Misconception You Hear?
Our expert breaks down a common misconception heard in the workspace regarding cybersecurity.
Datasheet - What Is Enhanced Data Protection?
Read about Dataprise's properety technology, enhanced data protection and how it can save your organization.
Blog Article - 2022 Cybersecurity Spending Trends
Take a look back at our blog from earlier this year highlighting tips to adopt a preventative cybersecurity mindset.
Have questions on how to implement best practice cybersecurity measures in your organization?
Contact us to speak with our cybersecurity experts.